How to use Burp Suite with multiple profiles in Firefox
August 27, 2019
There is a few popular ways to run Burp Suite in the pentesting environment. The simplified approach is to have a dedicated web browser to use (only) with Burp.
The downside is that the proxy setting for the browser (Chrome and Safari) needs to be set on the system level - on the Mac OS X. As a result, the whole HTTP and HTTPS traffic from the system would be routed through Burp and not only traffic from the browser but also traffic from the installed applications.
Proxy configuration in Firefox is set directly in the browser. There is no need to modify system settings.
Multiple Firefox profiles
Firefox allows creating separate profiles acting as containers storing sensitive information separated from each other. Each profile stores its own:
- Cookies
- Extensions
- Security certificate settings
- and more...
"Security certificate settings: The cert9.db file stores all your security certificate settings and any SSL certificates you have imported into Firefox."
Burp requires cacert.der (CA cert) to be imported in the browser or system keychain (not recommended) to intercept HTTPS traffic. If attacker would get this certificate and MITM your connection (i.e., when using public Wi-Fi) he would get your whole traffic, unencrypted.
That is why storing this certificate in your browser, is not a good idea, because it opens up a new attack vector. If you are curious about what might happen, read about a similar case from Dell: eDellroot issue
On every new installation or when Burp's configuration is wiped out, it would generate a new CA certificate served from "http://burp/cert" URL. It significantly makes the attack harder from the malicious actor perspective.
Thanks to Firefox and its multiple profiles, we can install cacert.der only in a separate profile and keep the default one without Burp's CA certificate.
That allows running two Firefox instances, side by side with each other. Furthermore, you can install all of the necessary plugins in Burp's Firefox profile, and it will not affect the default one.
Read more on Firefox profiles.
Configuration
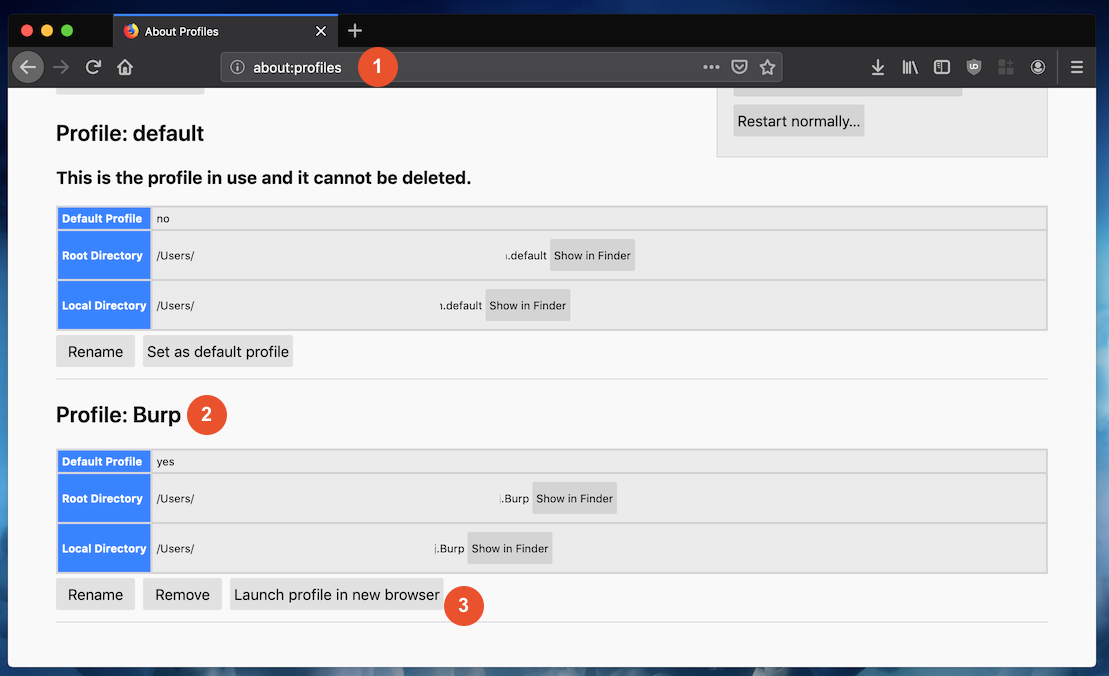
- Open Firefox and go to "about:profiles" URL
- Create a new profile and name it "Burp"
- Click on the "Launch profile in new browser" button
- New Firefox window should Open
- Install Foxy Proxy extension if needed
- Change Firefox theme to easily distinguish between "default" and "Burp" profiles
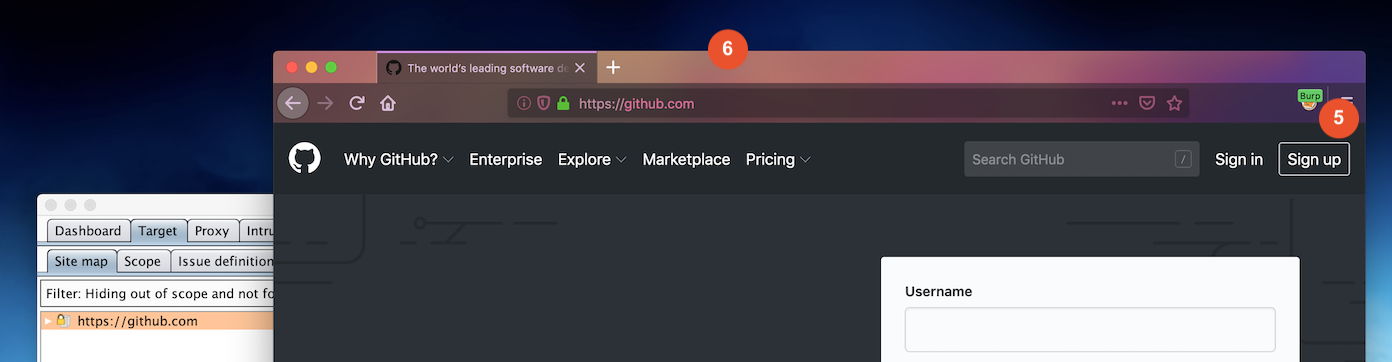
Whenever you want to run "Burp" profile open Firefox and go to "about:profiles" to launch it, there is an option to use CLI to run a profile as well.
/Applications/Firefox.app/Contents/MacOS/firefox-bin --profilemanager
Takeaways
- Do not install
cacert.derin your (default) web browser, especially do not install that directly into the system keychain - Always separate your pentesting tools and activities from your day-to-day environment/configuration
- If possible, run Burp inside virtual machine or on the remote instance to avoid embarrassing incidents if someone hacks you through the Burp Suite installation. Software is software, and vulnerabilities do happen